Remote Desktop Connection Xp Patch
I just installed the latest Windows update (NSA vulnerability patch tuesday) and now I cannot connect to remote desktop. The server is remotely hosted. I don't have physical access. Server 2012 R1.
- Setup Remote Desktop Connection Xp
- Remote Desktop Connection Xp Patcher
- Remote Desktop Windows Xp Home
Fortunately all web sites are running ok after reboot. I have not yet tried a second reboot because I'm a little scared to. When I try to connect I immediately get this message:.
' Remote Desktop Connection: An internal error has occured'. Have tried from multiple clients. I would love to tell you - but I just ran windows update and then it rebooted - and now I can't get in. 'Latest updates' that win 2k wanted to update is unfortunately all I can reveal of the mystery.
I've been playing Theater 3000 all day trying to think of a strategy. Chances are if I get the hosting company to reboot it will be fine, but that feels like I locked myself out of my home and I'm sending a locksmith while I won't even be there. Thank God I have remote access for SQL server / FTP and all websites are running ok. If there's a command to run to see the updates I can try that–Apr 17 '17 at 1:12. The solution is basically hereThis helped too:Assuming you have already verified that the certificate listed under Certificates Remote Desktop Certificates isn't valid.Note: I took this screenshot after I fixed everything - so this expiration date is the newly created cert that it did all by itself.You basically then need to rename or delete this file - and then it will recreate it:'C:ProgramDataMicrosoftCryptoRSAMachineKeysf686aace6942fb7f7ceb231212eef4a4a54b3870-f13c-44bb-98c7-d0511f3e1757'This is a well-known filename beginning in f686aace.
Then restart the Remote Desktop Configuration service and it should recreate it. (Note: it may actually not be necessary to restart the service - just wait to see if it is recreated with the same filename for a minute).It may take some messing around with permissions and you may need to take ownership of the file and then in addition apply permissions. Note: Ownership doesn't imply permissions. You must add permissions after taking ownership.As I said I don't have physical access to the server - if you do then the above should suffice.I was fortunate to be able to connect remotely via another machine on the same local networkand change the registry.I wanted to DISABLE authentication so I could connect and gain access remotely. The registry entries to do this are HKLMSYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-TcpSet the existing keys SecurityLayer and UserAuthentication to 0Create an RDP file (open mstsc and click Save after entering the servername) and in notepad add the line enablecredsspsupport:i:0 somewhere. This disables the expectation of security.When you then run the RDP file it should allow you to UNSECURELY connect and gain access to your server.As soon as you connect change these two registry entries back and then go ahead and delete the f686.
Setup Remote Desktop Connection Xp
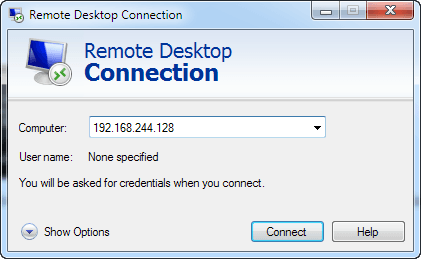
Remote Desktop Connection Xp Patcher
These settings fixed my issue:1.In Control Panel, click Administrative Tools, and then double-click Local Security Policy.2.In Local Security Settings, expand Local Policies, and then click Security Options.3.Under Policy in the right pane, double-click System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing, and then click Enabled. In my case it was disabled. So I just enabled it and issued the under listed command. Run gpupdate /forceAnother option which will solve this problem:The protocols were not enabled on the server. I used IIScrypto and enabled TLS1.2 and everything started working. Hello everyone in my environment this was caused when a new self signed certificate was generated TLS 1.0 is either disabled in the registry or does not exist in the registry and the new self signed cert was not in the trusted root certification authorities store.You can prove this two ways before editing the registry.
Remote Desktop Windows Xp Home

Download IIS Crypto and see what is enabled and disabled in Protocols, Ciphers, Hashes, and Key Exchanges.Sometimes though IIS Crypto will show that TLS is enabled even though it is not enabled in the registry just an FYI.Your next option is to turn on FIPS in Local group policy this forces TLS 1.0, 1.1, and 1.2 to be turned on and used. Turn on FIPS and then try to RDP into your machine it will work this time even if TLS is disabled in the registry.
Top News
- ✔ Dolby Virtual Surround Sound Software Download
- ✔ Call Of Duty 1 Maps Download
- ✔ Remotely Deployable Keylogger
- ✔ Adobe Photoshop Cs5 3D Materials Download
- ✔ Download Grand Chase Offline Version Of Diablo
- ✔ Cyberlink Power Media Player Keygen Free
- ✔ Shukriya Shukriya Mp3 Song Free Download
- ✔ Cfa Level 3 Secret Sauce Pdf
- ✔ Twonav Download
- ✔ Grmculfrer Es Dvd Iso Player
- ✔ Kriya Yoga Of Babaji 144 Techniques Pdf